Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayThe threat of cyber attacks is greater than it ever was. And, with increased automation of network systems, SCADA security is a topic of increasing concern for network operators.

SCADA systems monitor and control mission-critical equipment and infrastructure. It's important to prevent the unauthorized interception of data or the malicious injection of bogus or harmful traffic.
As a developer of network alarm monitoring solutions, we have a long history of protecting access to your alarms, and we understand that the consequences of attacks on your SCADA system could impact core system operations. We know how important it is to make sure that your data is private and that only authorized people can access your SCADA devices.
Fortunately, there are three major attack prevention approaches that you can implement to help protect your SCADA system.
The first SCADA attack prevention strategy involves securing the SCADA communications transport.
At individual sites, individual sensors collect values from inputs and outputs, which are referred to as SCADA points. These values are sent from individual sensors to the RTU, which forwards these SCADA communications to the central master station.
SCADA networks utilize a number of different ways to conduct these communications.
Early SCADA communications took place over radio, modem, or dedicated serial lines. In today's SCADA systems, the trend is to put data on Ethernet and IP over SONET. For security reasons, SCADA data is frequently restricted to closed LAN/WAN to avoid exposing sensitive information to the open Internet.
To ensure SCADA security, you could potentially extend their secure LAN to all of your remote sites. However, this is a very expensive technique, as extending LAN all the way out to remote sites just to achieve SCADA security can be an extremely expensive process.
An alternative solution to this costly solution is to deploy RTUs capable of working with both LAN and fault-tolerant dedicated serial lines. You can utilize the same RTU devices to provide SCADA security at all of your sites. This prevents expensive LAN installation when serial lines are available, or purchasing new RTU devices once the LAN has expanded.
Your RTU should meet all types of SCADA security needs, and grow along with the LAN network to provide security, regardless of a site's network connection.
Communications between the main office and remote access points are a vital part of a network monitoring system.
Without the ability for a technician to access the database of alarms and activities, or for the administrator to edit permissions and usage restrictions, you may as well as be attempting to run a SCADA system with no visibility.
While, allowing wide open access from across the network is out of the question, many people have tried to implement various security measures to verify the user attempting to gain access. That's where the RADIUS feature comes in.
Remote Authentication Dial In User Service (RADIUS) technology is an industry-standard authentication method. It provides a way to manage logins to many different types of equipment in one central location.
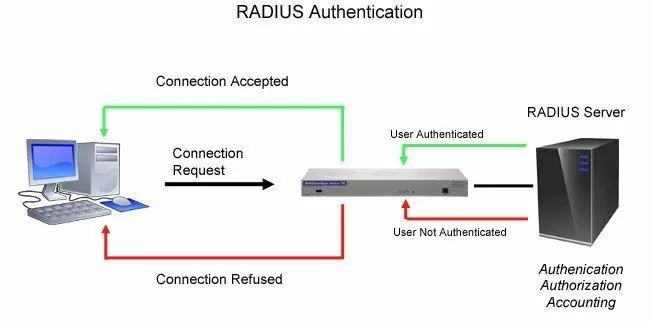
Using the client/server format, RADIUS passes user information to designated servers and acts on the response that is returned.
The tasks of the server include receiving client requests to connect, authentication of the user, and the return of configuration information necessary for the client to deliver services to the user. While serving as a proxy client, a RADIUS server can allow the client to connect to other RADIUS servers or other kinds of authentication methods, such as PPP, PAP, UNIX login, as well as several other methods.
In other words, every time a device receives a login attempt - usually a username and password - it requests an authentication from the central RADIUS server.
A user login consists of several steps:
Query (Access-Request)
Response (Access-Accept/Reject/Challenge and corresponding parameters)
Reply (client acts upon information received by server)
Another built-in feature of RADIUS authentication methods is the ability to account for all attempts at access, authorization, and user activities while utilizing one of the many client devices.
With the RADIUS capability, you gain several key security advantages for your SCADA system:
Virtually Unlimited Users
With RADIUS, the number of user logins you can support is huge. It's almost impossible that you'd ever run out.
Centralized Management
You'll also be able to manage your logins from your central RADIUS server. You'll never have to worry about updating any single remote. If an employee leaves your company, you can revoke their access rights right away.
Integration with Enterprise Management
When your RTUs use the same RADIUS authentication method as your other important gear, you significantly reduce the complexity of managing your equipment. It's always easier to manage a single system than it is to try to keep track of multiple unrelated systems.
RADIUS technology provides tougher authentication for government, military, and large private firms.
Viruses and web browser security holes aren't dangers that affect only ordinary PCs. Any network equipment that supports a web interface might face these threats.
Although this is changing more and more each day, the reason for this vulnerability is that most web-based communication is not encrypted. Of course, this is isn't an issue if you're just reading the news. However, when it comes to the web interface of your SCADA equipment, you've got critical alarm information - as well as control relays - that you need to protect.
Network operators are growing concerned that fundamental SCADA network equipment might be vulnerable to Internet-based attacks. One of the best practice standards is to protect your SCADA system equipment from open Internet access.
To secure your alarm monitoring web interfaces, make sure that your SCADA system equipment supports the HTTPS/SSL encryption feature - aka Secure Web Interface.
The Secure Web Interface is the ideal alarm monitoring interface for on-call technicians who need to view alarms details from home, technicians who need to verify alarms and corrections from remote sites, as well as for supervisors who need to check network statuses from their desks or from the road.
This software module supports Hypertext Transfer Protocol over Secure Socket Layer, the industry-standard secure web protocol for online sales and financial transactions.
So, for instance, when a remote access user connects to your master station using HTTPS, the web server establishes a secure connection to the user's web browser. Data passing through the secure connection is encrypted, protecting information from being intercepted.
If users connect to the SCADA unit from both inside and outside the company firewall, you can use HTTP or HTTPS connections at the same time. But, if you do, make sure to configure your router to block the HTTP port (typically port 80), so that to one outside your network can access unencrypted information.
To connect to your SCADA unit over HTTPS, normally all you have to do is type "https://" followed by the IP address of your system into the address bar of your web browser. When connected, the web browser window will display a lock icon to indicate a secure encrypted connection. You can log on and use your system as usual, with complete security.
Managing SCADA network security is more than simply making sure that everyone on the network has the correct firewall or antivirus installed.
Managing your SCADA network's security also means protecting your network's physical resources and ensuring that your hardware-based security devices are always up and running. You'll have to secure your network not only from online attacks, but from physical ones as well, so your SCADA system is always available for staff and clients to access.
With your SCADA system and mission-critical gear at stake, even at your unmanned sites, you can't rely on an old-fashioned lock-and-key system for security. Not only do locks get picked, but a tech who forgets his keys while on a trip to a remote site will waste time and fuel going back. Even if he doesn't forget his keys, finding the right one is a waste of time when a single proxy card or key code can be configured to let the user access sites as needed.
The best practice when deploying an access control system to manage entry at your sites is to join it into your present remote monitoring networks. This will reduce complications and costs.
Consider having proxy readers or keypads at sites housing gear only some personnel should access. And you may even want to employ an IP camera to deter threats and catch those responsible in the event of a physical breach.
To control building access, the best practice is to install Entry Control Units (ECU) at every door with access to your SCADA network resources. You can manage access with an ECU by keypad, proxy reader, or motion sensor. Make sure that your ECU can be connected to the serial ports on your RTUs. This way your RTUs will store access profiles from your master station and issue control logic for the ECU units at your doors.
At sites where you don't have an RTU, or simply don't need RTU functionality, but still need building access control, you can install door control gear that talks directly to your master station or NOC.
Also, make sure that your IP cameras can be joined into your building access system as well. This camera should be configurable to capture images on a "trigger," such as motion or a door-breach alarm. Not only will the cameras help deter intrusion at your sites, but if someone does attempt to circumvent your network's physical security, you can capture their picture.
Plus, make sure that notifications for things such as breaches, open doors, and other sorts of alarms can be sent to you via email, text message, pager, or even voice alerts if you so choose.
While physical SCADA network security is every bit as important as info security, there's no reason that managing your physical resources has to be hard. Find a secure and robust network of RTUs and a solid master station that can both alert you when you're having a SCADA network-equipment related failure and control building access.
There's a lot you can do to protect your SCADA system. Your sensitive and important alarm data should never be vulnerable to outside attacks. Simple precautions and the right vendor can provide you with the secure equipment to truly protect your network.
As a provider of monitoring and control customized solutions, we make sure to always design a reliable and secure system for collecting and managing your SCADA information. So, we offer several technologies that are favored by security-focused companies and government agencies, including:
We also take advantage of being a vertically integrated manufacturer to customize any of your devices to fit your security needs.
For example, for one security-conscious client we created a one-way protocol and removed control relays from the device. This allowed their remote sites to report information to their master, without their master being able to control or access their sites. This prevented any hacker from gaining control over the equipment in their SCADA network.
If you want devices that follow the previous top three security best practices, but don't know where to start, or if you simply want more technical details, just reach out to us at DPS. Even if your security need is unique, we can work together to create a specific solution just for you.

Morgana Siggins
Morgana Siggins is a marketing writer, content creator, and documentation specialist at DPS Telecom. She has created over 200 blog articles and videos sharing her years of experience in the remote monitoring industry.