Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayData security is a critical business priority no matter your industry. After all, you don't want viruses, malware, or hackers to have access to your information.
The same is true if you have a remote monitoring system deployed to give you viability over your network. Monitoring systems collect real-time information and can even allow you to remotely control equipment. So, it's vital that you keep it safe from ill-intended people.
At DPS, we provide monitoring solutions to many different industries, and we aim to provide top-notch safety to all of them - from government agencies to small companies with simple networks. With more than 30 years in business, it's safe to say that we have plenty of experience when it comes to efficient data protection.
So, to help you ensure that your information is completely secure, we've put together the following list of questions. Ask yourself those questions and assess your level of network security preparedness.
Is your remote monitoring system designed in a way that the most secure option is the default?
If your answer is no, then that's your first step. A remote monitoring system that was designed with security in mind is one of the best ways to protect your data. This is because safe processes will help minimize any breaches or data loss.
In fact, a network that was designed especially with security features in mind will take you a step further and lead you to better outcomes.
Also, can you say your system's users are trained to follow the most secure processes and take the safest actions? Make sure to properly train the team working with your monitoring system. Remember, your system's users are one of your biggest security assets.
Continuing the topic of your employees, how much information can each person in your team access?
There is no reason for a person to have access to information (or receive alerts) that it's not useful for them. Many people in your company may need access to your remote monitoring system data but only approved staff should have access to the underlying system, its controls, and the configuration database.
Security parameters usually include:
Usually, network technicians can view and acknowledge alarms, while network managers are able to edit the system database. Only the highest level of system administrators should access to the entire monitoring system.
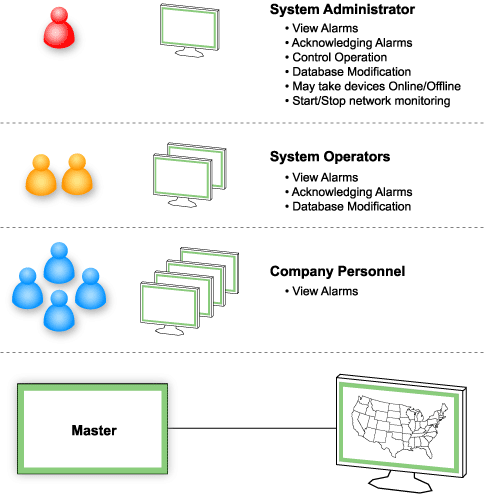
Making sure you have a safe multi-user access makes your alarm monitoring more efficient. You can share the access to viewing alarm data with your team without the worries of compromising information.
Also, securing your data and only giving access through role-based permissions with authentication measures, such as usernames and passwords, will help you reinforce your system's security. And, remember, that these access permissions should be updated regularly to make sure the data they protect remains on a need-to-know basis.
Many government agencies need remote monitoring systems for a number of reasons, and making sure their data is secure is a priority. For that, many agencies choose to deploy monitoring systems with SNMPv3-enabled devices.
SNMPv3 is the most advanced version of SNMP. It brings a higher level of security because it features:
Encrypting your network information with SNMPv3 is an important best practice (even if you are not a government agency).
Once you have remote monitoring that implements all the previous security measures (or if you already have it), it's time to ensure that they remain effective.
Test your security features and evaluate them under controlled conditions. Compare the assets that you need to protect the most with all the potential threats that they can succumb to. What's the probability of these threats to happen and how is your remote monitoring system vulnerable to them?
Testing your safety procedures will give you a better insight into the weaknesses that might be present in your system and how you can possibly deal with them.
If you haven't deployed your monitoring system yet or if you are looking for safer alternatives to what you already have, investing in the T/Mon LNX is a great way to safeguard your network.
T/Mon LNX is a powerful monitoring master station that can provide you with many security features, such as:
Other T/Mon's productivity-enhancing features are:
If you need some special kind of security feature we can certainly integrate it into your T/Mon device. In fact, if you need any kind of customization, don't be afraid to treat us as your own personal engineering department - that's what we specialize in.
Our monitoring devices are designed and built at our headquarters in Fresno, so providing you with a perfect-fit solution is easy for us. So, give us a call and tell what us what your network requirements are.

Morgana Siggins
Morgana Siggins is a marketing writer, content creator, and documentation specialist at DPS Telecom. She has created over 200 blog articles and videos sharing her years of experience in the remote monitoring industry.