Download our free SNMP White Paper. Featuring SNMP Expert Marshall DenHartog.
This guidebook has been created to give you the information you need to successfully implement SNMP-based alarm monitoring in your network.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat Today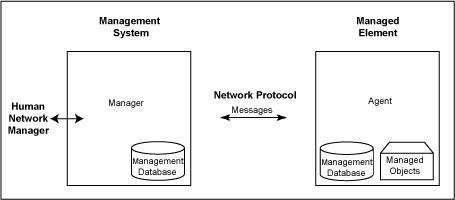
Since its creation in 1988 as a short-term solution to manage elements in the growing Internet and other attached networks, SNMP has achieved widespread acceptance as an internet protocol.
SNMP was derived from its predecessor SGMP (Simple Gateway Management Protocol) and was intended to be replaced by a solution based on the CMIS/CMIP (Common Management Information Service/Protocol) architecture. This long-term solution, however, never received the widespread acceptance of SNMP.
Part of why the protocol has reached such wide adoption is due to the fact that it is an open standard. While there are widely accepted standards, there is no governing body that controls how SNMP can and cannot be used, or declares and set rules for how messages are created and processed, making it extremely flexible and unable to be made obsolete by a singular vendor going out of business.
SNMP is based on the manager/agent model consisting of a manager, an agent, a database of management information, managed objects and the network protocol. The manager provides the interface between the human network manager and the network management system. The agent provides the interface between the manager and the physical managed devices (see illustration above).
The manager and agent expose management data in the form of variables called Management Information Base (MIB) and a relatively small set of commands to exchange information. The MIB is organized in a tree structure with individual variables, such as point status or description, being represented as leaves on the branches. A long numeric tag or object identifier (OID) is used to distinguish each variable uniquely in the MIB and in SNMP messages.
MIB files are vendor-specific but are community-based. They define how the vendor's devices understand OIDs and respond when one is received. For example, without the DPS-specific MIB file, a device can still receive a trap, but may not know what it means or what to do in response to it.
To date, there are three major versions. SNMPv1 is the original and is still supported by our products. SNMPv2c and v3 offer additional flexibility and security, introducing features such as community strings. The choice for which version you should use is ultimately up to you and what your network monitoring needs are.
SNMP can do a lot to make your network alarm monitoring more cost-effective and your network more reliable - if you clearly identify your network monitoring goals and have the right tools to achieve them.
The advantages of SNMP are:
That's what's good about SNMP - but there's also some pitfalls that you have to watch out for. If you're not careful, it's easy to wind up with a system that costs too much and does too little.
You can avoid the risks (and guarantee the benefits) of your SNMP implementation by working with an experienced vendor who can help you accurately determine your network monitoring needs. To learn more, call 1-800-693-0351 and ask for your free Network Monitoring Needs Analysis.