Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat TodayAs data centers evolve with more sophisticated processes and technologies that are driving up physical demands, their environments need to be looked at more closely. Safeguarding against digital threats only is not enough - the surrounding environment must be watched proactively for threats and intrusions.
Remote network locations further highlight the need for an automated monitoring system. After all, at those sites, it's impractical and unreliable to have people physically present to check conditions such as temperature and humidity. It's critical for you, as a network technician or manager, to have an efficient system in place to know what's going on.
With today's technologies, monitoring systems can be configured to a level of detail that meets the data center's particular environmental and security demands. Each equipment rack can be considered a "mini data center" with its own requirements, so you need to a have monitoring strategy in place that supports multiple data collection points.
In this article, we'll talk more about how physical threats can be mitigated by monitoring strategies. You'll also learn guidelines and best practices for implementing monitoring devices in your facility. So, let's dive in.
Dangers and problems found at data centers can be classified into two main categories, depending on whether they are in the area of software and networking (digital threats) or in the realm of the physical support infrastructure (physical threats).
When we talk about digital threats, we are referring to things such as hackers, viruses, network bottlenecks, and other accidental or malicious assaults on the security or flow of data. These issues have a high profile in the industry, and most companies have robust and actively maintained systems to defend against them.
Physical problems are the ones related to your IT equipment and to your data center infrastructure. These threats can potentially be distributed anywhere throughout your data center, at variable locations that are particular to room layout and equipment positioning.
Some of the distributed physical problems fall into the following general categories:
The first step to start monitoring your data center is to deploy sensors throughout the facility to gather information.
There are multiple types of sensors that can be used to provide early warning of trouble from the threats described above. While the specific types and number of sensors will vary depending on your unique scenario (in terms of what you need to monitor, budget, threat risk, etc.), there is a minimum essential set of sensors that makes sense for most data centers. They are:
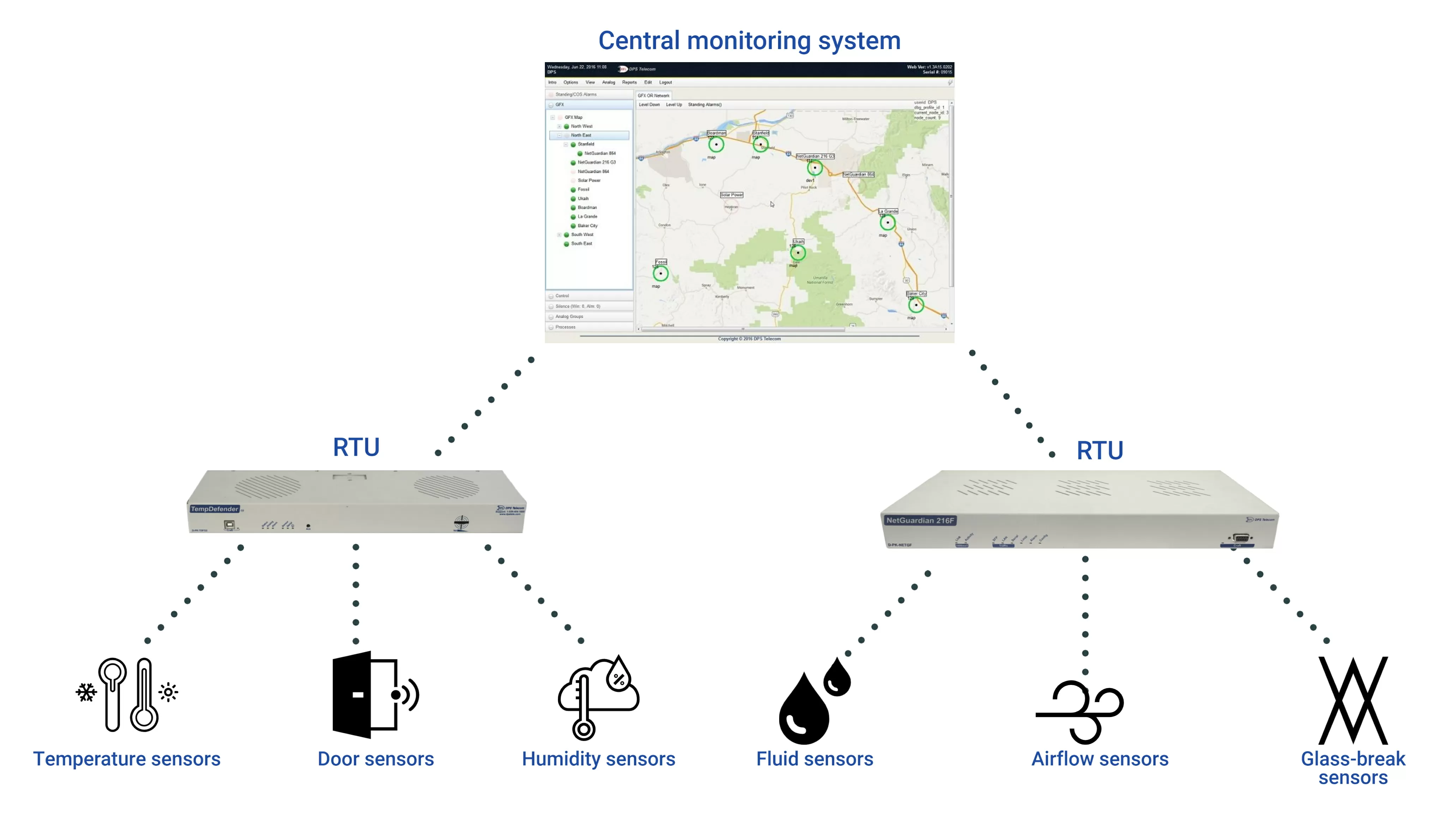
With the sensors selected and in place, the next step is the collection and analysis of the information received by the sensors. This is will be done by an RTU (or by multiple RTUs, depending on your needs). It will be an aggregation point where sensor data will be gathered and processed.
If your network is large enough, the RTU unit will send all the information to a central master station (that will manage the information brought by multiple units). If that's not your case, and all you need is a couple of RTUs, then your unit can be used as a single central collection point with alert and notification capabilities.
Individual sensors don't usually connect individually to the IP network. Instead, the RTU interprets the sensor information and sends alerts to the central master station and/or directly to you and your team. This distributed monitoring architecture drastically simplifies your network monitoring and reduces the management burden.
RTUs are typically deployed at the facilities your equipment is located and when paired with D-Wire sensors there will be no wiring complexity.
Sensors supply the raw data, but equally important is the interpretation of this data to perform alerting, notification, and correction. As networks become more and more sophisticated, having an efficient monitoring strategy with intelligent processing of large amounts of data is critical.
The most effective and efficient way to collect and analyze sensor data and trigger appropriate action is through the RTUs as described above.
It's essential to be able to filter, correlate, and evaluate the data to determine the best course of action when out-of-bounds events happen. Effective action means alerting the right people, via the right method, with the right information.
Action is taken in one of three ways:
There are three things to establish when setting alerts: alarm thresholds (at what values should an alarm be triggered), alerting methods (how the alert should be sent and to whom), and escalation (do certain types of alarms require a different level of escalation to resolve?).

Collecting sensor data is only the first step, and if you, as the network technician, rely on user responses alone, the information will not be leveraged to maximum advantage. There are systems available that act automatically based on user-specified alerts and thresholds. For our devices, these automated responses are called derived controls.
In order to implement such smart automation, the following must be assessed:
Alerting systems should provide more than just basic threshold violation notifications. For example, our monitoring systems allow you to include additional data with the alerts. This additional information might be things like instructions on how to fix the issue, graphs, or maps. A rich alerting system of this type allows you to make more informed decisions because of the contextual data included with the alert.
In some cases, too much information may need to be filtered to be useful. For example, if you're responsible for a high-traffic data center, it would be a nuisance to have an alert every time a motion is detected in the facility. There may be instances where critical information will be lost in a sea of nuisance alerts. Thinking about this issue, our monitoring devices are equipped with the nuisance alarm filtering capability.
Now, here are some examples of intelligent interpretation and action:
Intelligent monitoring systems should include not only short-term trending of sensor data but also long-term historical data as well. The best monitoring solutions should have sensor readings from weeks, months, or even years past and provide the ability to produce graphs and reports of this data.
The graphs should be able to present multiple types of sensors on the same report of comparison and analysis. The reports should be able to provide low, high, and average sensor readings in the selected time frame across various groups of sensors.
Long-term historical sensor information can be used in a variety of ways. For example, to illustrate that the data center is at capacity not because of physical space, but due to inadequate cooling, Such information could be used to extrapolate future trends as more and more equipment is added to your data center, and could help predict when the data center will reach capacity. Long-term trending analysis could be used at the rack-level to compare how equipment from different manufacturers in different racks produce more heat or run cooler, which may influence future purchases.
Sensor readings captured by the monitoring system should be exportable to open-standard protocols, allowing interoperability between your devices.
Protecting your data center against physical threats is crucial to a comprehensive security strategy. But, you need to find the proper devices that will provide you with real-time monitoring, data logging, trend analysis, intelligent alert notifications, and automated corrective actions where possible.
While the placement and methodology of monitoring equipment require assessment, decision, and design, at DPS we provide tools that follow the industry's best practices and that are available to help you in an effective monitoring system deployment.
Understanding the techniques for monitoring physical threats will enable you, as the network technician, to fill critical gaps in your overall data center security. Ultimately, you'll be able to help your company have a better ROI and achieve its business goals.
For more information about our physical monitoring equipment, send us a message.

Morgana Siggins
Morgana Siggins is a marketing writer, content creator, and documentation specialist at DPS Telecom. She has created over 200 blog articles and videos sharing her years of experience in the remote monitoring industry.