Check out our White Paper Series!
A complete library of helpful advice and survival guides for every aspect of system monitoring and control.
1-800-693-0351
Have a specific question? Ask our team of expert engineers and get a specific answer!
Sign up for the next DPS Factory Training!

Whether you're new to our equipment or you've used it for years, DPS factory training is the best way to get more from your monitoring.
Reserve Your Seat Today
|
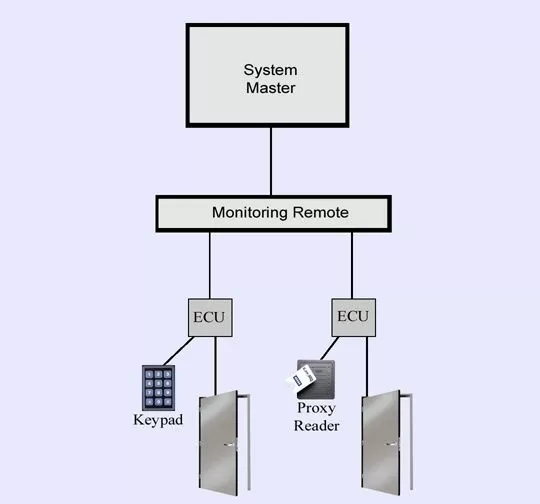
When users enter access data into these input devices, it is verified by the Entry Control Unit (ECU) on the interior of the site directly behind the proxy card reader. If the user is validated for access, the door will ECU will then release the door strike.
Each of these individual access attempts is recorded, combining the information with the time and point of access. This data flows upward through the monitoring system, and is collected by the system master. The master is then able to create detailed history logs of every access attempt, and provide alarm notifications to your operators whenever necessary through a single interface.
Integrating building access controls into a network alarm monitoring system allows you to simply utilize their existing master browser to monitor their building access events. Your technicians simply connect access devices such as keypads and proxy card readers to their system, and the system master will automatically collect the access data.
The system master can provide detailed reports on these access events. This can be particularly useful in the event of theft or vandalism at one of your sites. This data can be combined with network alarm data as well, letting you know immediately if a visitor to your site has tampered with your mission-critical equipment.
You need a system that can be tailored to the unique access needs of your important sites. At DPS Telecom, this custom design is a standard service. Our business has been built on continuous innovation, and we embrace opportunities to design new monitoring solutions.
Our integrated building access systems are backed by a 30-day, no-risk guarantee. Test the proposed solution under real-world conditions for 30 days, and if, at any time during that period, you decide for any reason that our solution will not meet your access control needs, you can cancel your order with no further obligation. It sounds crazy, but in the 15 years we've offered our no-risk guarantee, not one client has returned a custom solution.
|